Findings Reveal Both the Increased Importance of Mobile Apps and the Relative Lack of Focus on Runtime App and Data Protection; July 26 Webinar Will Reveal Additional Findings.
Key Takeaways:
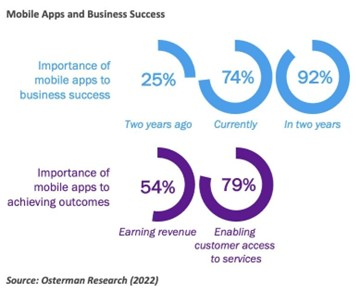
- Three out of four respondents report that mobile apps are now “essential” or “absolutely core” to their success: This is three times higher than two years ago.
- Secure development practices are essential but offer only partial protection: They do not eliminate the threat of runtime attacks against mobile apps and APIs.
- Run-time attacks against APIs that render mobile apps non-functional prove costly to 75 percent of organizations: Attacks include data theft and service interruption via API abuse, fake account creation, and credit fraud, among others.
- Most lack visibility into runtime threats against mobile apps and APIs: Sixty percent of organizations report that they do not have visibility to runtime threats against mobile apps and APIs.
- Reducing threats resulting from hardcoded API keys is a priority: With about half of mobile apps storing API keys as hard-coded secrets, the use of more than 30 third-party APIs per mobile app creates a significant runtime threat space. Fifty-five percent of respondents place high priority on removing the need to store API keys and other hard-coded secrets in mobile apps.
- Accelerating time-to-market for new features is prioritized over security: One half of respondents report that for competitive reasons, their organizations may ship apps with known insecurities, and two fifths of respondents report that their organization’s security processes for both third-party and in-house developers are weak and insufficient.
Approov, creators of advanced mobile app and API shielding solutions, today issued, “The State of Mobile App Security in 2022,” a new report from Osterman Research. The report codifies the increasing dependence of businesses upon their mobile apps, and reveals a jarring disconnect between the strategic importance of apps versus the level of focus and resources applied to protect organizational apps against runtime threats.
This press release features multimedia. View the full release here: https://www.businesswire.com/news/home/20220714005251/en/
(Graphic: Business Wire)
Michael Sampson, Senior Analyst, Osterman Research, said: “Mobile apps are key channels through which businesses serve their customers, and their importance to organizations has tripled in the last two years. Our research reveals that while enterprise app development and deployment are among an organization's highest priorities, unfortunately, the runtime security of the app, its API secrets and the user data collected do not receive similarly high prioritization and budget. These findings raise serious questions, given that so many recent breaches have highlighted the risk of stolen keys and secrets being exploited by threat actors.”
Osterman Research surveyed 302 security directors and mobile application development professionals in the US and UK. Forty-eight percent of respondents are in companies of up to 500 employees, 42 percent are in companies of 501 to 4,999 employees, and 10 percent are in companies of more than 5,000 employees.
Among key findings:
- Mobile Apps Are Increasingly Important to Business Success: The importance of mobile apps to business success has tripled over the past two years. Three out of four respondents indicate mobile apps are now “essential” or “absolutely core” to their success, up from one out of four two years ago.
- Three out of Four Organizations Would Face Substantial Consequences from a Successful Attack on Their Mobile App: An attack against APIs that rendered a mobile app non-functional would have a significant effect on 45 percent of businesses and a major impact on an additional 30 percent.
- Low Confidence in Mitigation Against Specific Threats: Seventy-eight percent of respondents are not highly confident that their organizations have the appropriate level of security defenses and protections in place to protect against specific threats posed by mobile apps.
- Poor Visibility into Security Threats Against Mobile Apps: Sixty percent of respondents lack visibility into credit fraud attempts, 59 percent lack visibility into the creation of fake accounts, 56 percent lack visibility into data stolen from PIs by scripts and 54 percent cannot detect the use of stolen API keys being used to mimic genuine requests. Moreover, 53 percent lack visibility into credential stuffing attacks, 51 percent lack visibility into secrets exposed on mobile platforms, and 50 percent cannot detect access by cloned, fake or tampered apps.
- Third-Party APIs Create Pathways for Threat Actors: On average, mobile apps depend on more than 30 third-party APIs, and half of the mobile developers surveyed are still storing API keys in the app code, constituting a massive attack surface for bad actors to exploit. Third-party API threats against mobile apps aren’t as well understood by companies as they need to be. Third-party developers are not required to attest to following required standards at 42 percent of organizations, penetration testing is not conducted to evaluate the security of third-party code (at 38 percent of organizations), and the security of third-party APIs integrated into mobile apps is not vetted at 35 percent of organizations.
- Although Mobile Apps in Production Are Vulnerable to Threats Unmitigated During Development, Runtime Threats Nevertheless Receive Lower Priority and Funding: The report finds that despite the recognition that protecting mobile apps and APIs at runtime is an enduring requirement, spending is still skewed towards “shift-left” and respondents indicate their organizations place the highest priority on secure development practices.
David Stewart, CEO of Approov, said: “This research reflects the overarching fact that although mobile apps are an increasingly critical conduit for both commerce and communications, investment in runtime protection of apps and APIs continues to take a back seat. Moreover, poor practices continue unabated, such as the storing of hard-coded keys in a mobile app or device, which exposes app secrets to increasingly clever threat actors.
“Given that mobile apps and APIs are increasingly the lifeblood of organizations, the practices and resource allocation towards runtime threats must be reconsidered – and quickly – before yet another wave of major mobile app breaches exposes both organizations and their customers to the damage and continual loss that inevitably result.”
Approov recently added a Runtime Secrets Protection capability to the Approov Mobile App Protection platform, a convenient SaaS service that manages and protects all the secrets a mobile app uses, and delivers secrets “just-in-time” to the app only at the moment they are required to make an API call, and only when the app and its runtime environment has passed attestation. It was developed to ensure that sensitive API secrets are not being continuously stored or delivered to unsafe places, such as fake apps or into malicious hands, and marks a major security improvement over keys that are hard-coded in the app itself.
Please visit https://approov.io/for/state-of-mobile-app-security-2022/ to download “The State of Mobile App Security in 2022” or sign up to attend a webinar on the findings with report author Michael Sampson, Senior Analyst with Osterman Research, and David Stewart, CEO of Approov. Michael will present his findings at 2 p.m. ET on July 26, 2022.
About Approov:
Approov solutions help stop API abuse at the edge, and prevent security breaches in mobile channels. With more businesses moving to digitalization and future-ready services that utilize mobile API connections, securing those connections properly can get overlooked or not fully implemented for all possible threats, exposing organizations and their users to breaches, fraud, denial of service, and other forms of API abuse.
Approov API Threat Protection provides a multi-factor, end-to-end mobile API security solution that complements identity management, endpoint, and device protection to lock-down proper API usage. It ensures that only safe and approved apps running in safe environments can successfully and securely access an organization’s APIs, and turns away unauthorized accesses by attacker scripting, bots and fake or tampered apps. https://www.approov.io/
View source version on businesswire.com: https://www.businesswire.com/news/home/20220714005251/en/
“Mobile apps and APIs are the lifeblood of organizations. The practices and resource allocation towards runtime threats must be reconsidered – quickly – before yet another wave of major mobile app breaches exposes both organizations and their customers."
Contacts
Dan Chmielewski
Madison Alexander PR, Inc.
714-832-8716
C: 949-231-2965













